Source: Orange Cybersecurity Security Navigator 2022 report
- Orange Cyberdefense helicopters to the heights to analyse the increasing incidence of cyber and ransomware attacks
- Comprehensive and very well-designed report but what a whopper!
- Security is a journey, not a destination: You’ll never get there, but you'll get closer if you keep moving
- To minimise trouble, form alliances, share best practices and intelligence, and set common security policies
Orange Cyberdefense, an arm of one of the world’s biggest telcos that provides security services to support multinationals and smaller businesses internationally, has just published the third edition of its Security Navigator report, and, at 92 pages, it’s big ‘un. The 2022 iteration, subtitled 'Research-driven insights to build a data-driven society', is jam-packed with enough facts, diagrams, schematics and statistics to satisfy the even nerdiest cyber security executive who dons an anorak and doubles as a train spotter and bus ticket collector at the weekends.
Hugues Foulon, the executive director of Strategy and Cyber Security at Orange Group, points out that as the lockdowns and disruption caused by Covid-19 pandemic begin, to some extent, to ease (or maybe not, given the developments of the last week or so?) many businesses may be confronted with the need, quickly, to lock down their own infrastructure as cyber and ransomware attacks proliferate. Such a shut-down strategy involves accepting temporary damage and disruption to avoid something even worse, and inevitably, given the interconnected and interdependent business world of the 21st Century, this can have a domino-effect on supply chains. Indeed, “Attacks like SolarWinds and the Kaseya incident have proven us one clear point: even trusted software from reliable vendors can turn into a trojan horse for cunning attackers.”
He adds, “Technology alone cannot be the solution to this problem. To face this situation, we should be conscious of the fact that no one is facing these challenges alone. Anyone can be a victim on an individual or collective level. We as the global digital community, must join our efforts to stand against these threats. This is not an easy journey. Cyber security is complex. Fragmentation of options in the industry makes the problem more challenging, and at the same time different organisations require different solutions depending on their current stage, context and future ambitions.”
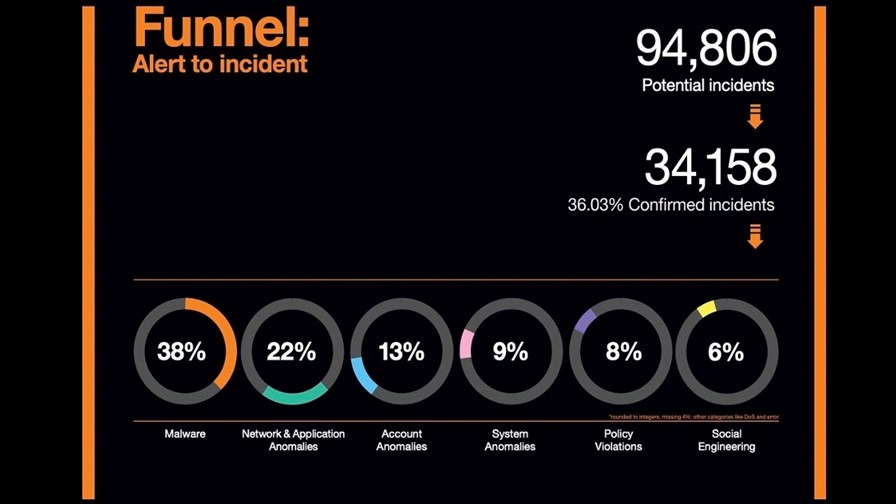
The new report is a synthesis and distillation of analysis undertaken by Orange’s 18 Security Operations Centres (SOCs) and 14 CyberSOCS that analysed over 60 billion security events daily, investigated in excess more than 94,000 potential security incidents, and led more than 230 incident response missions during the past 12 months.
Report confirms malware and ransomware attacks as spreading like err, well, like a virus
The new report covers a wide range of sectors and businesses and confirms what many others have also reported; that a significant shift in cyber attacks has taken place over the past year, with more than 30 per cent of all confirmed cyber incidents in 2021 having been directly associated with, and classified as, malware (see chart above). Orange Cyberdefense’s intention is detect potential incidents early to prevent them developing into full blown ransomware attacks and the report also shows that when the global volume of ransomware increased during late summer, Orange Cyberdefense detected an increased incidence of first stage attacks that could, potentially, have been an even more serious threat.
Back in the spring, medium- and large-sized organisations reported similar levels and intensities of attacks but SMEs suffered a consistent increase in malware incidents. The report says that does not necessarily mean small organisations are attacked more often, but find it harder to cope when they are because they lack the experience and resources to defend themselves against relentless adversaries attacking with a set of advanced tools.
The report also provides a check list of what to do in event of an incursion and stresses the immense importance of managing the first hour of response to a critical incident. To be able to do that effectively it is essential to prepare and have robust procedures in place and ready to deploy to counteract immediately. The next step is to ascertain what really happened and shut the the gaps, nooks and crannies through which malware can gain entry - and always remember the dictum of Sherlock Holmes, “Once you eliminate the impossible, whatever remains, no matter how improbable, must be the truth.” Or, put another way, “It couldn’t get in that way"... "Oh yes it could!”
The cyber-threat environment is as complex as it is plastic and evolving. The number of individual “actors” and groups involved is increasing in number and expertise. Only a few major and powerful gangs are responsible for about 50 per cent of all malware and ransomware attacks, and about half or those (or perhaps more, it is difficult to be sure) are so-called “state actors” operating on behalf of nation states such as China, Iran, North Korea or Russia. Simultaneously, more and more individuals and small groups are becoming involved.
The report says a mere 10 per cent of companies and organisations suffering ransomware attacks actually pay a ransom, but the sums involved can be very high (if they are ever revealed at all) and those individual and groups of cybercriminals that do get paid off make a lot of money and then move on to another target, or, as is happening more and more often, return to their earlier victim to extort a second or even a third payment.
It takes organisations time to get over an attack and, currently, about 60 days to remediate them, during which time they remain vulnerable to another attack. Meanwhile, the emergence of Ransomware-as-a-Service gangs is a disturbing development. Here, gangs go to ever greater and more novel lengths and use tactics such as launching DDoS attacks, emailing clients and media, auctioning stolen data and trying to impact the share price, to force victims to pay.
Microsoft-based systems the most vulnerable - with Google a close second
In the IT world, Microsoft is still at Number One in terms of the sheer raw number of vulnerabilities, with Google coming a close second. Simultaneously, IoT vulnerabilities increase with every deployment in an immature sector where security is still often an afterthought and attackers can all the more easily exploit weak spots.
The Orange Cyberdefense report concludes that cyberdefense must be looked at more strategic level, with the first item on the agenda being to reduce complexity and understand that security, by its very nature, is a continuing journey not a destination. The reality is that you’ll never get there, but you will get closer if you keep moving. To help, defenders should form alliances, share intelligence and best practices, and and set common security policies. For far too long cybercriminals have profited because organisations and companies have acted alone in response to attacks -- it would be much better and more effective to form a united front to face a common enemy.
The Orange Cyberdefense Security Navigator report, “Research-driven insights to build a data-driven society”, contains too much detailed information and case studies to cover here in a single article. You can read the whole thing for yourselves here: It’s well worth it, despite a few infelicities in the English translation.
Email Newsletters
Sign up to receive TelecomTV's top news and videos, plus exclusive subscriber-only content direct to your inbox.




