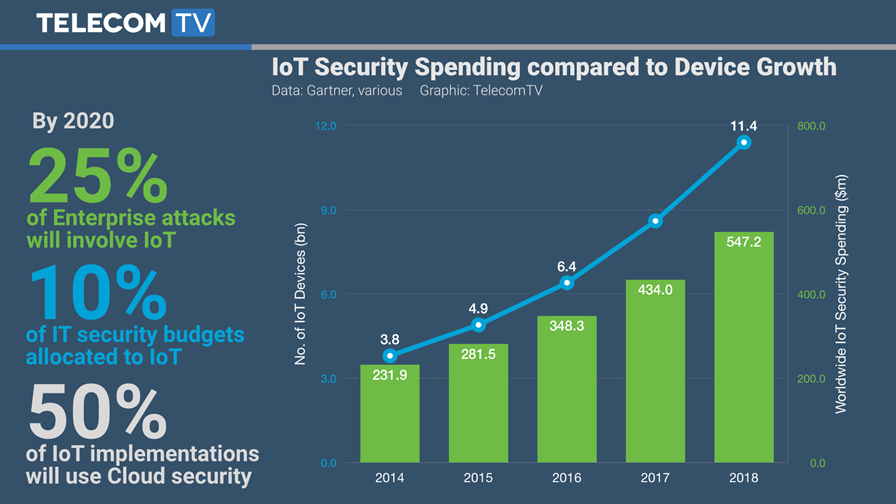
© Gartner / TTV
After the euphoria of the potential of the Internet of Things (how many billion devices?) comes the practical reality – nobody will use them and connect to them if they are not secure. Unlike the smartphone revolution, IoT devices will, in the main, be relatively cheap low-cost items, and they’ll be manufactured and sold by a huge range of vendors. Easy then, to cut corners and overlook important security aspects.
Not only that, but the network configurations and deployment schemes envisaged give rise to some potentially dangerous cyberattack opportunities. For example, enabling user access control at IoT endpoints is vulnerable to replay, “man-in-the-middle”, and denial-of-service (DOS) attacks.
A new proposal from the IEEE, published in the current “Proceedings of the IEEE” journal, suggests a model that combines the capabilities of smart IoT devices with control system gateways using real-time challenge response for secure control operations. Both endpoint and gateway devices would employ a mix of compute, cryptography, signal/image processing, and communication capabilities for authentication and authorisation functions. The new model would be more secure, scalable, and resilient with real-time performance as compared to traditional approaches.
Real-Time Identity Monitoring
IEEE members and Intel executives Michael Condry and Catherine Blackadar Nelson have come up with the proposal, which creates an added level of security beyond initial authentication. This “Real-Time Identity Monitoring” can monitor the connection for certain known client device behaviours or regularly request additional authentication verification information.
“Most smartphones contain gyroscopes, thermometers, photometers, barometers, magnetometers, and sensors for acceleration, gravity, rotational vector, humidity, orientation, proximity to device, gestures, and sometimes heartrate,” explain the authors. “Any of these can be used to monitor a change in the user’s environment. By using a combination of sensor data from the client and known good behaviours, a user baseline can be generated. Any deviation from this baseline could trigger a request for reverification of the user’s identity, or even close the connection.”
For example, if the user’s heart-rate suddenly went up, it is possible that the user was under some type of stress like a device hijacking, or the proximity sensor could tell if the device became separated from the user and may be being used by a third party.
Increasingly, control systems are becoming networked, and access control to the gateway becomes critical. A 2013 study by Trend Micro found that the largest number hacking attempts against a monitored “honeypot” control system were categorised as “unauthorized access”.
Most security problems now occur around user authentication and authorization. WThe authors suggest that with the increase in compute, storage, and connectivity capabilities of IoT devices, these challenges can be addressed by combing the functionality of control system gateways with those of the client IoT devices. Security capability can be further enhanced by using Real-Time Identity Monitoring, which when combined with Multifactor Authentication (MFA), offers a more secure environment than traditional solutions.
If IoT is to play a lead role in the Industrial Internet and Industry 4.0, then a better framework for standards in security is needed
Email Newsletters
Sign up to receive TelecomTV's top news and videos, plus exclusive subscriber-only content direct to your inbox.




