
via Flickr © alexbrn (CC BY 2.0)
- Samsung alterations leave A50 smartphone more vulnerable to hackers
- Expert implies that Samsung is not the only offender
- Sales of devices with hardware security jumped 39 percent in 2019
One of Google's top security experts has warned that tweaks made by Samsung to Android's underlying code can leave devices more vulnerable to hackers.
Jann Horn gained fame a few years ago by single-handedly discovering major security flaws in the design of well-known processors. These days he is a member of Google Project Zero, a team tasked with finding zero-day vulnerabilities in software.
In a blog post last week, Horn detailed how one modification to the Android kernel implemented by Samsung on its Galaxy A50 – a modification seemingly intended to make the smartphone more secure – actually introduces bugs that make it less so.
Called PROCA, it appears designed to limit an attacker who has already gained read/write access to the kernel.
"[It] seems futile, and engineering resources would have been better spent preventing an attacker from getting to that point in the first place," Horn wrote.
He provided a comprehensive technical explanation of how PROCA can be exploited to potentially allow an attacker to gain access to sensitive data stored on the device. He noted that the alterations made by Samsung meant that the A50 is even susceptible to an old Android bug that was fixed by a patch more than a year ago.
"In my opinion, some of the custom features that Samsung added are unnecessary, and can be removed without any loss of value."
The tone of Horn's article implied that the Samsung example is just the tip of the iceberg. No other vendors were named, but it can be inferred that this is not an isolated incident.
"The way Android device branches are currently maintained is a security problem," Horn said.
The case also highlights the difficulty Android OEMs face when they try to differentiate by adding features – however subtle – to the operating system.
Android has become more locked down over the years, as Google seeks to ensure the quality and security of the OS. This is understandable. It doesn't want Android's reputation tarnished by phone makers bringing out shoddy products that don't work properly or worse, that leave customers vulnerable to hackers.
The industry has its work cut out trying to protect Android users though, which would explain Samsung's motive.
According to McAfee's most recent threat report, more than 1.5 million new malware programmes were identified in the first quarter of 2019.
"Mobile malware running on the Android operating system is the most prevalent at this time, driven by the ease of installing new applications from third-party sources," noted Crowdstrike in its 2019 Mobile Threat Landscape report.
Indeed, rogue apps are one of the most common ways for a user to unwittingly install malware on their handset.
Crowdstrike also warned that mobile antivirus software is less mature than its desktop equivalent, making it easier for attackers to access a mobile device undetected.
As a result, Android OEMs are increasingly using hardware to enhance the security of their products.
Counterpoint Research released a report last week showing that one third of all smartphones sold in 2019 had embedded hardware security, which represents a 39 percent increase on 2018.
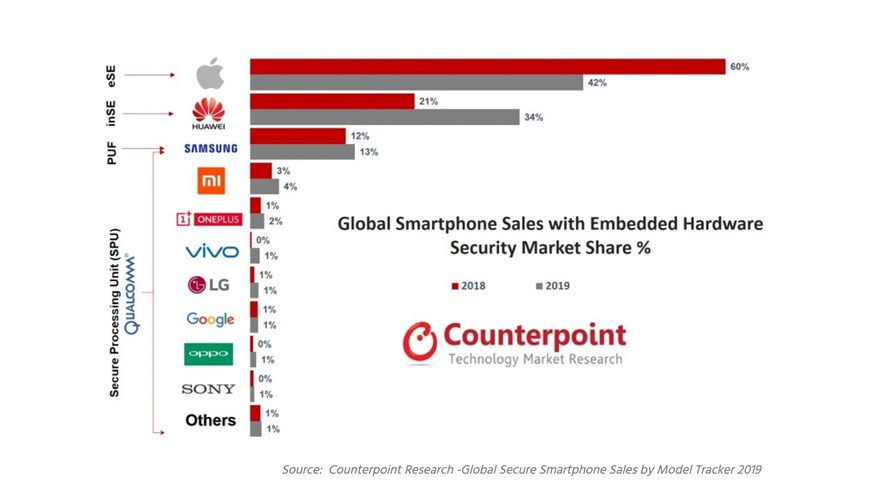
via Counterpoint Research, February 2020
"The secure element is a coprocessor within the SoC which assures tamper-resistance and is capable of securely hosting applications," said Neil Shah, vice president of research at Counterpoint.
Different vendors have different ways of implementing the technology, he explained, but they all share the common goal of making it harder for attackers to compromise devices and gain access to sensitive data.
"Secure chipsets like secure elements, PUFs (physical unclonable functions), and TPMs (trust platform modules) embedded in the smartphone are currently the best solution to meet increased security needs," said Counterpoint Research analyst Satyajit Sinha.
With that in mind, poking around in Android's code – however well-intentioned – seems unwarranted, and that when it comes to security, hardware-makers should continue to focus on what they do best: hardware.
Email Newsletters
Sign up to receive TelecomTV's top news and videos, plus exclusive subscriber-only content direct to your inbox.




