New Arm IP helps protect IoT devices from increasingly prevalent physical threats
May 02, 2018
By Paul Williamson, Vice President and General Manager, IoT Device IP Line of Business, Arm
News highlights:
-
New Arm Cortex-M35P processor, first Cortex-M to combine anti-tampering technology and robust software isolation – bringing smartcard levels of security to emerging applications such as smart metering, door locks and automotive
-
Enhanced security IP protects silicon against increasingly prevalent physical attacks by bringing higher levels of protection against close proximity side-channel attacks, including power and electromagnetic analysis
-
Together, the new suite of IP empowers Arm partners to achieve a flexible and robust level of physical security enabling emerging IoT use cases
At Arm TechCon last year, we published the Arm Security Manifesto and were very clear that to reach the vision of one trillion connected devices by 2035, security is no longer optional. This has never been more evident in the evolving state of IoT security, where malicious entities are increasingly using more novel techniques for compromising connected devices.
IoT security is a multi-faceted problem with billions of diverse devices requiring a system-wide approach for protecting them. The diversity in this space is challenging for our partners, and today we’re announcing new products that provide a critical layer of system protection by empowering SoC designers to incorporate higher levels of security, in the growing set of applications that require protection against physical attack threats.
In the past, it was harder to justify protecting against physical attacks beyond payment applications. However, as IoT gains momentum and more devices with high-value data become connected, the physical attack surface becomes more attractive to hackers. This is amplified by the availability of tools and education, which make these physical attacks cheaper and easier to make a reality. To protect the IoT, we need to think beyond software attacks and physical security requires our attention more than ever. As new use cases emerge, this protection won’t just be required for payment and identity applications, it will need to be integrated for use cases such as smart lighting, connected door locks, smart meters or automotive applications.
Defining “physical attacks” and where they fit in the device threat spectrum
Before diving into product details, I’ll give you some brief context and definition of physical attacks. These are attacks that could be a result of direct, physical contact with the device SoC or close proximity to it. This significantly differs from attacks such as Mirai, which was an exploitation of default passwords, or vulnerabilities like Spectre and Meltdown, which require malware to be loaded onto the device remotely.
Physical attacks aim to exploit vulnerabilities at the silicon implementation level, rather than exploiting a software or design level weakness. These physical attacks fall into two main categories: invasive attacks, requiring (at least) chip de-packaging, and non-invasive attacks, for example close proximity side-channel attacks (SCA), which gain information through unintended side channels stemming from the silicon implementation (for example through observing the chip’s power consumption or electromagnetic field emission during a cryptographic operation). Both attack classes have similar goals - retrieve sensitive information processed within the chip or simply cause it to carry out unintended behaviour, serving the attacker’s goals.
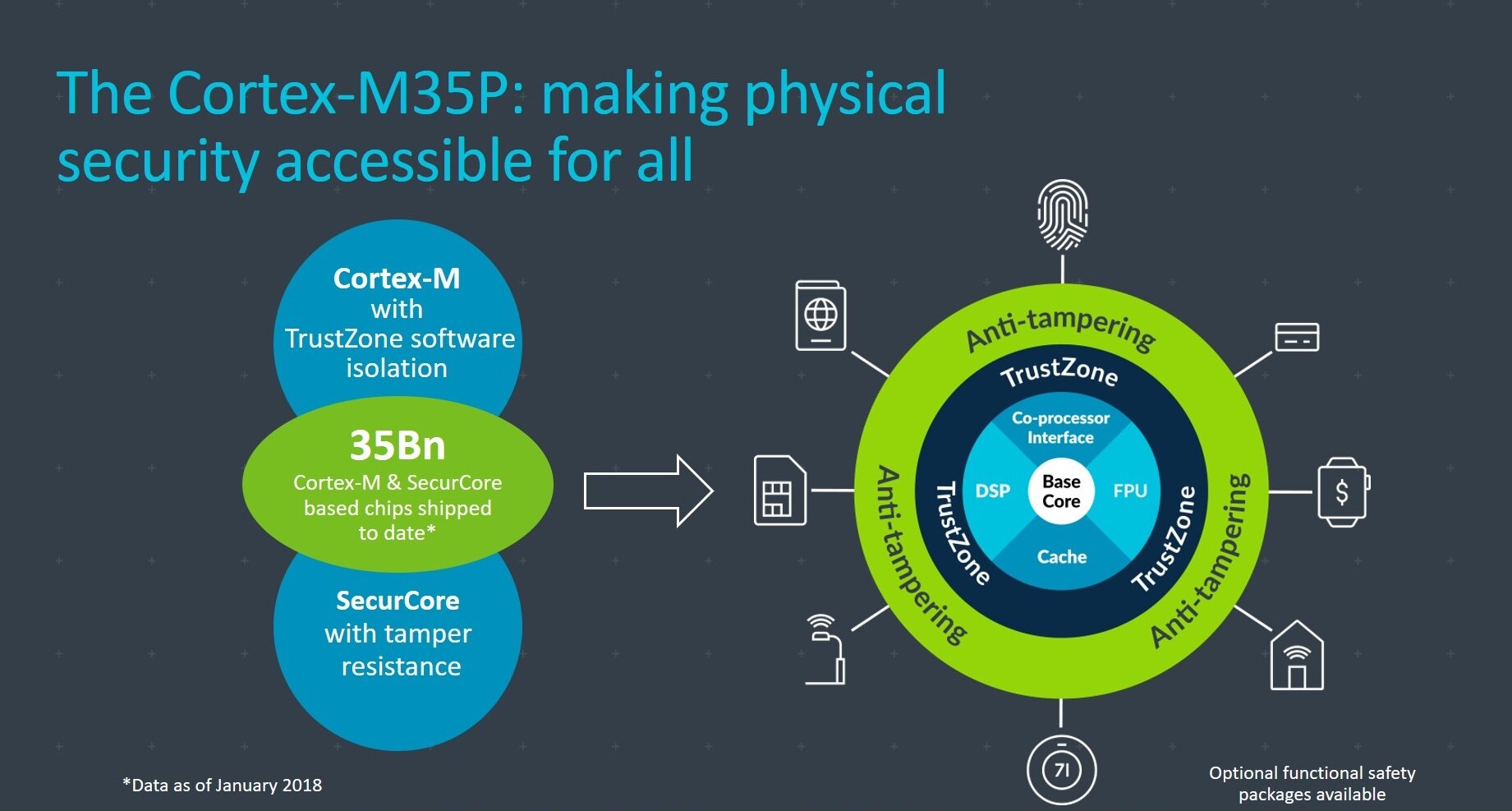
The new Cortex-M35P processor: making physical security accessible for all developers
Moving forward, all Arm secure IP designed to protect against physical attacks will be designated with a “P” tag for physical security. The Cortex-M35P is a robust, high-performing processor that enables embedded security developers to hinder physical tampering and achieve a higher level of security certification.
-
It’s the first processor in the Cortex-M family with designed-in tamper resistance
-
Built on the industry proven anti-tamper technology used in Arm SecurCore processors that have been deployed in billions of devices to date, primarily in smart/credit card applications.
-
Includes Arm TrustZone technology for robust software isolation, making it easier and faster for designers to embed multi-layered payment or telecom-certified security at the core of any device.
-
If functional safety is a requirement, Cortex-M35P can also include a safety package to support ISO 26262 certification.
Beyond the CPU, Cortex-M35P is an extension of Arm’s comprehensive security portfolio, following the principles of Arm's Platform Security Architecture (PSA). You can read more about the Cortex-M35P in this blog.
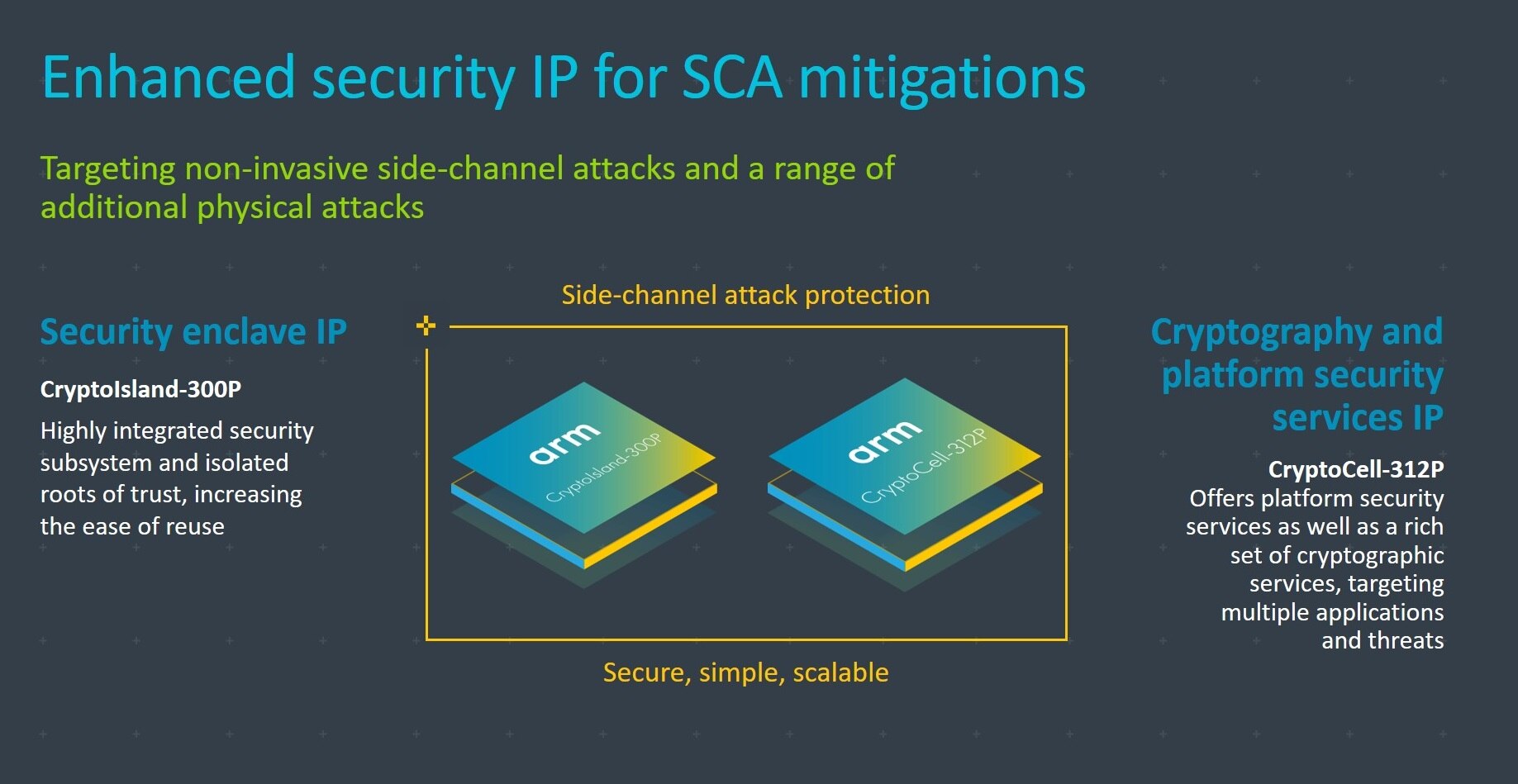
Arm CryptoCell-312P and Arm CryptoIsland-300P: Enhanced security IP with SCA mitigation
Today we’re also announcing that two key pieces of our existing security IP, CryptoCell and CryptoIsland, are available with technology to protect against a range of SCAs (including power and electromagnetic analysis), allowing partners to license a hardened version of the IP in our security portfolio. The CryptoCell and CryptoIsland solutions have been addressing the security needs of different stakeholders along the value chain for quite some time now. With the addition of physical attack resistance, these solutions can address an even broader attack surface, required by some IoT applications.
With the addition of physical security to these products, Arm has taken a unique approach to SCA protection. By mitigating information leakage at the source, rather than looking for ways to hide or mask the leaking information, we have put an additional safeguard in place for protecting against evolving methods and analysis tools attackers might use to overcome traditional ‘information hiding’ tactics. It also means our mitigation method is not dependent on the nature of the underlying functionality that gets protected, so it can scale from market to market.
A secure IoT demands that we mitigate a wider scope of attacks
As new IoT use cases emerge, physical security requires the industry’s attention more than ever. This protection won’t just be required for payment and identity applications, it will need to be integrated into smart lighting, connected door locks, smart meters or automotive applications.
For example, if one smart streetlight or building smart light is hacked, an entire city’s smart lighting grid or company’s enterprise is potentially vulnerable. Physical security, in emerging applications, is one part of a system level approach to secure devices as defined in our Platform Security Architecture (PSA). Another critical aspect is managing device software through its entire lifetime, and this is where the Arm Mbed IoT Device Platform plays a critical role. You can read more about how Arm is enabling secure smart lighting through a complete system approach in this blog.
As I previously mentioned, the design of Cortex-M35P follows the principles of PSA which state that in defining device security requirements, we first need to analyze the specific use cases for the IoT device. This allows us to assess the associated assets and their value, before defining the various attack surfaces that may pose a threat to the new device. From there, designers can determine a layered approach for implementing the right levels of security and threat-mitigation technology.
The new IP we’re launching today adds to our already robust security portfolio and equips our partners with more building blocks and more flexibility to form the right security solution for their application and market, offering protection for both existing and emerging use cases that require physical resilience at their heart.
Email Newsletters
Sign up to receive TelecomTV's top news and videos, plus exclusive subscriber-only content direct to your inbox.



